Context
One of the most popular scams throughout industries is the Business Email Compromise (BEC). BECs are responsible for many notable real world scams, incurring hundreds of millions of dollars of losses from 2013 to 2014 alone.
I’ll be handling my own BEC situation, where a malicious actor has sent phishing emails to many employees, trying to trick them into sending hundreds of thousands of dollars. To stop this, I’ll be looking at some potentially malicious emails and inspecting .pcap files to determine which emails are legitimate and which ones are fraudulent.
Core Concepts
Log analysis and correlation of events
- Inspect PCAP files / Inspect email traffic
Analysis Technique
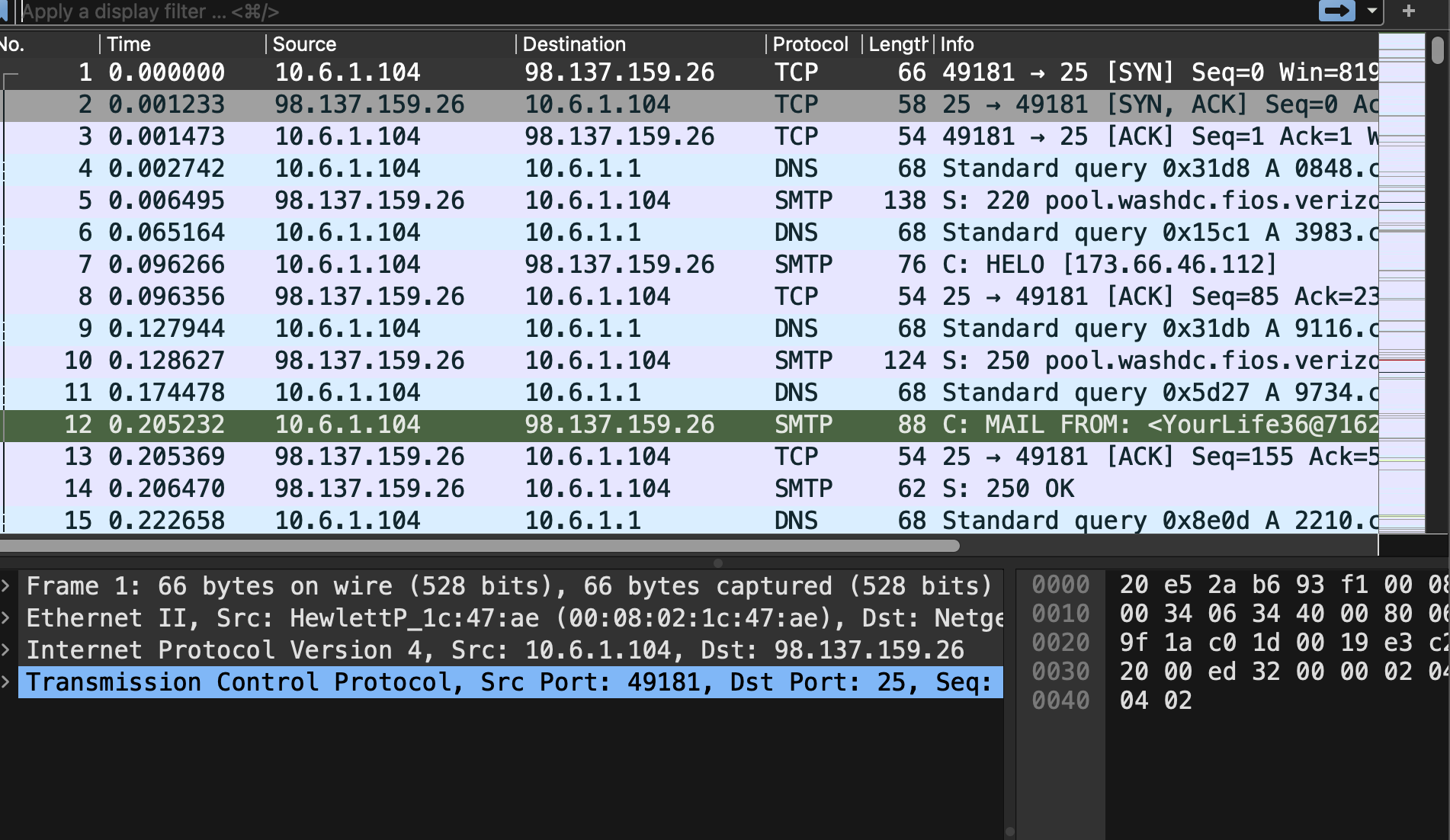
Tools: Wireshark, SMTP display filter commands
- Download the
pcap_files.zipwhich contains multiple.pcapfiles taken on different days. - Download Wireshark
- Utilize Wireshark to Analyze the contents of the
.pcap- Useful Techniques
“smtp contains "FROM”– this command helped me to sort out the actual senders of the mail transfer from other network traffic; helping me identify what I was looking for.- Downloading data tagged
smtpas an.emlfile.emlallows the actual email contents sent over the network to be visualized (this made it really helpful in terms of analyzation because wireshark itself failed to paint a complete picture.
- Changing my settings to get rid of the information that was not relevant by adjusting the dashboard became important as I narrowed down my search.
- Useful Techniques
- Identifying the Malicious Actor
- Actor #1: Links and a hidden email of
“xxxxx@...”I assumed that this was malicious and trying to phish people into clicking the email, but was not convinced. Inspecting further led me to the actual suspect.
- Actor #2: email address with a bunch of spam coming out was actually the malicious IP. That made sense. When I looked into the emails, I realized the messages were the same. The messages stated that malware had been installed on the users computer, and that bitcoin was required for payment to avoid any negative outcomes.
- Actor #1: Links and a hidden email of